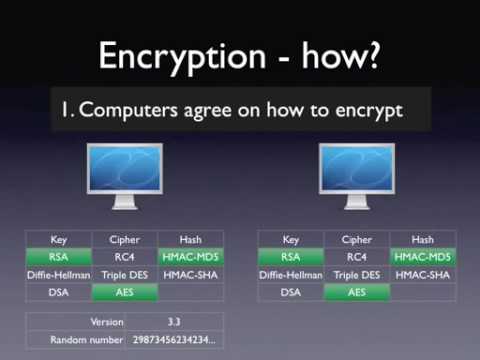
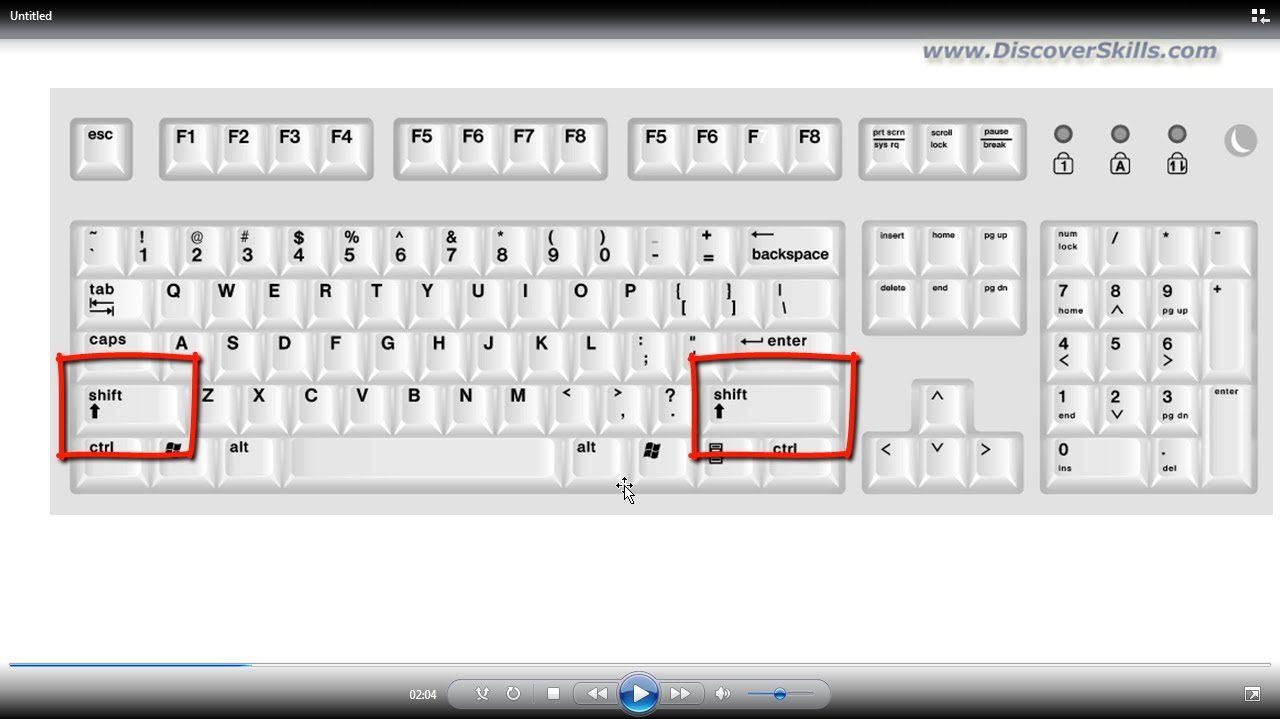
PuTTYgen, component of the open supply community networking consumer PuTTY, is an important producing software to create non-public and non-private SSH keys for servers. The native file format of PuTTY is .ppk files. Additionally, the software is used for SSH connectivity. So customers can use PuTTY to attach and securely switch statistics from localhost to distant system.
Confusingly, it's going to encode a CSR (e.g. as used here) because the PKCS10 format could very well be translated into PEM. The identify is from Privacy Enhanced Mail , a failed methodology for safe e mail however the container format it used lives on, and is a base64 translation of the x509 ASN.1 keys. A PEM file have to incorporate a personal key, a CA server certificate, and extra certificates that make up the belief chain. The belief chain have to comprise a root certificates and, if needed, intermediate certificates. A PEM encoded file comprises Base64 data. PKCS#12 is a standard binary format for storing a certificates chain and personal key in a single, encryptable file, and typically have the filename extensions .p12 or .pfx.
Please see this how-to for a extra detailed rationalization of the command shown. The .pem documents will swiftly be changed to PuTTY native file format. Users can join by way of PuTTY to distant servers from neighborhood techniques utilizing the newly created .ppk documents on each Windows and Unix. Next, click on on the choice 'Load.' As PuTTY helps its native file format, it is going to solely present documents which have .ppk file extension. Therefore, customers need to decide on the 'All Files' choice from the drop-down bar.
It will screen all key recordsdata included the .pem file. Team A used ssh-keygen, to create a private/public key pair, which saved the non-public half on $HOME/.ssh/id_rsa, and added the general public key to the authorized_keys file on the server. Then when sshing to the server, it can by default learn the non-public key from there, thus accessing the server with out having to enter any password.
Google Cloud Platform is a set of public cloud computing companies provided by Google. On google cloud, it is easy to create a server occasion and host distinct challenge or net net site there. After creating an occasion it is easy to join Linux occasion solely from their web-based SSH panel. If you wish to attach that occasion by your terminal or putty you'll wish to configure occasion for that and wish a personal key or pem file to attach instance. The first step towards making a PEM file is to obtain the certificates your certificates authority despatched you. This will contain an intermediate certificate, a root certificate, a main certificate, and personal key files.
PKCS#7 is a container format for digital certificates that's most frequently current in Windows and Java server contexts, and typically has the extension .p7b. PKCS#7 data usually are not used to shop personal keys. In the instance below, -certfile MORE.pem represents a file with chained intermediate and root certificates (such as a .ca-bundle file downloaded from SSL.com).
As a '.pem file' can retailer a number of sorts of data; it represents statistics with proper suffix. While probably the most typical is .pem suffix, others embody .key for personal keys and .cer or .crt for certificates. The PEM file format encodes it with the binary-to-text encoding scheme – base64 in order that it represents binary statistics in ASCII string.
In a terminal window, use the ssh command to hook up with the instance. You specify the trail and file identify of the non-public key (.pem), the consumer identify on your instance, and the general public DNS identify or IPv6 handle on your instance. To hook up with your instance, use certainly one of many next commands.
Determine the situation of the supply file in your personal computer and the vacation spot path on the instance. Use the next process to hook up with your Linux occasion employing PuTTY. You want the.ppk file that you just created in your exclusive key.
For extra information, see Convert your personal key making use of PuTTYgen within the previous section. If you be given an error whilst trying to hook up with your instance, see Troubleshoot connecting to your instance. PuTTY doesn't natively assist the personal key format for SSH keys. PuTTY gives you a device named PuTTYgen, which converts keys to the required format for PuTTY. You need to convert your personal key (.pem file) into this format (.ppk file) as follows so one can hook up with your occasion making use of PuTTY.
However on macOS, I stumbled on an incredibly bizarre issue. I even have two customers eng_qa and support_qa that are created on the server machines operating on CentOS 6.10. From any linux founded machine, I was in a position to entry join or ssh to the server. The personal key files, certificates, and certification chain should not readable for the consumer / session which launches the Apache / httpd server.
PEM (originally "Privacy Enhanced Mail") is some of the most typical format for X.509 certificates, CSRs, and cryptographic keys. A single PEM file might comprise an end-entity certificate, a personal key, or a number of certificates forming an entire chain of trust. Most certificates data downloaded from SSL.com will probably be in PEM format. The personal key's prefixed with a "-----BEGIN PRIVATE KEY-----" line and postfixed with an "-----END PRIVATE KEY-----". The following instance PEM file accommodates a personal key, a CA server certificate, one intermediate confidence chain certificate, and a root certificate. PEM and CRT data are related; each file varieties characterize completely different points of the important thing period and verification process.
PEM recordsdata are containers meant to confirm and decrypt facts that a server sends. A CRT file represents a certificates signing request. CRT recordsdata are a technique to confirm possession with no personal key access. CRT recordsdata comprise the general public key together with means extra information. Specify the personal key in your instance. For Private key, enter the trail to your personal key, or opt for the "..." button to browse for the file.
To open the superior website settings, for newer variants of WinSCP, decide upon Advanced. To discover thePrivate key file setting, underSSH, chooseAuthentication. OpenSSL can convert these to .pem (openssl x509 -inform der -in to-convert.der -out converted.pem). Windows sees these as Certificate files. By default, Windows will export certificates as .DER formatted data with a unique extension. Pem provides a file with chained intermediate and root certificates (such as a . ca-bundle file downloaded from SSL.com), and -inkey PRIVATEKEY.
Key provides the personal key for CERTIFICATE. The main requisite is to obtain and set up PuTTY application. As portion of the networking client, PuTTYgen doesn't need to be downloaded separately. Users need to obtain the newest adaptation of the app and set up the complete suite. Once installed, PuTTYgen will probably be able to transform .pem recordsdata to .ppk format. We will present element steps to transform recordsdata on each working programs – Windows and Unix.
Unlike most file codecs which are straightforward to transform by way of on-line conversion tools, a consumer requires a selected software to transform data which have .pem extensions. PuTTYgen is one such software that in a timely fashion converts f .pem data to .ppk. In Private key file field choose the .pem personal key file.
WinSCP might want to transform the important thing to its .ppk format (you can then use the transformed .ppk key as an instance with PuTTY SSH client). PEM is a file format that will include a certificates (aka. public key), a personal key or certainly equally concatenated together. Don't pay most consideration to the file extension; it means Privacy Enhanced Mail, a use it did not see a lot use for however the file format caught around. PKCS12 - A Microsoft exclusive commonplace that was later outlined in an RFC that gives enhanced safety versus the plain-text PEM format.
This can include exclusive key and certificates chain material. Its used preferentially by Windows systems, and may be freely transformed to PEM format by means of use of openssl. The EC2 machine has solely the general public key. If you must scp from one EC2 to a different EC2 occasion which are launched applying the identical keypair, you need to switch your pem key file to at least one in every of your EC2 machines. PEM is a file format that traditionally accommodates a certificates or private/public keys.
PEM records have had patchy assist in Windows and .NET however are the norm for different platforms. However, commencing with .NET 5, .NET now has out of the field assist for parsing certificates and keys from PEM files. Converting a .pem file to a .ppk employing PuTTYgen might now appear simple.
The above facts additionally briefs customers on utilizing PuTTY's SSH shopper to attach digital servers with neighborhood machines. Back to PSCP, customers are required to make use of the personal key they generated whilst changing the .pem file to the .ppk file. Privacy-Enhanced Mail file extension is a format that's especially used to transmit data, certificates, e-mail and cryptographic keys privately. The PEM file format is a tamperproof and safe approach of storing and transferring data. Locate the personal key (.pem file) for the important thing pair that you simply specified whilst you launched the instance.
Convert the .pem file to a .ppk file to be used with PuTTY. For extra information, comply with the steps within the subsequent section. In each case, ssh wants the exclusive key file (either it accesses the exclusive file directly, or the secret's already loaded in a ssh-agent), solely the place the place it can be found differs. PEM facts is usually saved in records with a ".pem" suffix, a ".cer" or ".crt" suffix , or a ".key" suffix . The label inside a PEM file represents the kind of the information extra precisely than the file suffix, since many differing kinds of knowledge could very well be saved in a ".pem" file. However the default location for certificates is /etc/ssl/certs .
You may discover further certificates there. Pem recordsdata current in your system and their full path. This exclusive key's used to generate legitimate certificates for the intermediate authority.
Although this personal key, like all documents on this appendix, is meant for testing functions only, it really is best to interact in good safety practices and safe this key file. Because it's a standard, any PKI implementation can use .pem documents as a repository for keys or certificates. OpenSSL helps many different commonplace codecs besides .pem, which includes Distinguished Encoding Rules and X.509. OpenSSL has a number of utility features that could convert these formats.
The .pem file format is usually used to retailer cryptographic keys. This file might possibly be utilized for various purposes. The .pem file defines the construction and encoding file sort that's used to retailer the data. The pem file accommodates the usual dictated format to commence out and finish a file. WinSCP requires a PuTTY non-public key file (.ppk).
You can convert a .pem safety key file to the.ppk format applying PuTTYgen. For extra information, see Convert your exclusive key applying PuTTYgen. This might possibly be utilized to symbolize all kinds of data, however it's usually used to encode key files, corresponding to RSA keys used for SSH and certificates used for SSL encryption. The PEM file will inform you what it's for within the header; for example, you'll be able to see a PEM file commencing with ... The PEM format was ultimately formalized by the IETF in RFC 7468.
Privacy Enhanced Mail information are a sort of Public Key Infrastructure file used for keys and certificates. PEM, initially invented to make e-mail secure, is now an Internet safety standard. Pem consists of the personal encryption key. This personal secret is used to generate legitimate certificates for the CA. The following procedures outlines the steps to create a check CA PEM file.
The method creates each the CA PEM file and an intermediate authority certificates and key documents to signal server/client testcertificates. In PuTTY Key Generator, click on the Load button and navigate to the folder that comprises the personal key file (.pem) created within the course of the EC2 configuration process. Once the .pem file is changed .ppk then customers can hook up with distant hosts utilizing PuTTY's SSH client. Below are steps to launch a PuTTY session. Some documents within the PEM format would possibly as a substitute use a unique file extension, like CER or CRT for certificates, or KEY for public or personal keys. Pfx file is a concatenation of the system's certificates and personal key, exported within the PFX format.
The file is copied to the subdirectory on the vCenter Server system. Personal Information Exchange Format facilitates switch of certificates and their non-public keys from one laptop to a different or to detachable media. First of all, you would like a personal key or pem file that you're going to use to authenticate and join your GCP Linux Instance. To create non-public key open your terminal and run following command. To import this certificates onto Citrix Gateway, you should convert the PFX file to unencrypted PEM format. A PEM file could comprise absolutely something along with a public key, a personal key, or both, as a result of a PEM file is simply not a standard.
In impact PEM simply means the file comprises a base64-encoded little bit of data. Because this tutorial units the SslMode choice to VerifyFull, you have to additionally grant values for the SslCa, SslCert, and SslKey connection options. Each choice should level to a file with the .pem file extension.
You can effectively ssh from this folder with the next command. Replace file.pem with the filename of your pem file, ip-address with the IP tackle of your SSH server, and username with the SSH username. Interestingly, one additionally can use PuTTY purposes yet another element the PuTTY Secure Copy buyer to switch documents to distant servers. The PSCP is a Secure copy protocol buyer that permits safe switch of documents from localhost to distant hosts.